Network security is crucial in safeguarding businesses and individuals from cyber threats in today's interconnected world. One of the critical components of network security is a firewall, which acts as a barrier between the internal and external networks, filtering and monitoring incoming and outgoing network traffic. Among various types of firewalls, one that stands out is the Stateful Inspection Firewall.
Stateful Inspection Firewall, also known as dynamic packet filtering, is a security technology that combines the benefits of traditional packet filtering and advanced inspection techniques. It goes beyond simply examining individual packets and considers the context and state of the network connection. Doing so provides enhanced security and greater control over network traffic.
Stateful inspection firewalls boast an array of powerful features. They perform deep packet inspection, scrutinizing not only the packet headers but also the payload contents. This enables them to detect and mitigate various types of attacks, including port scanning, denial-of-service (DoS) attacks, and application-layer attacks. Additionally, stateful inspection firewalls support access control lists (ACLs) and can enforce granular security policies based on source and destination IP addresses, ports, and protocols.
- Stateful inspection firewalls maintain a state table that tracks the state of each network connection passing through the firewall. This table stores information such as source and destination IP addresses, port numbers, sequence numbers, and more. By comparing incoming packets against the state table, the firewall can determine whether to permit or reject the traffic. This intelligent analysis ensures that only legitimate and authorized connections are allowed while blocking potentially malicious or unauthorized ones.
- Implementing stateful inspection firewalls brings numerous advantages to organizations. Firstly, their ability to maintain session state information allows for enhanced security as they can detect and prevent unauthorized access attempts. Secondly, these firewalls provide improved performance by reducing the processing overhead associated with packet filtering. Lastly, stateful inspection firewalls offer flexibility in handling complex protocols and applications, ensuring seamless connectivity for modern network infrastructures.
- Deploying stateful inspection firewalls requires careful planning and consideration. Organizations should conduct a thorough network inventory to identify the optimal placement of these firewalls. They should also define clear security policies and configure the firewalls accordingly. Regular monitoring and updates are essential to adapt to evolving threats and maintain a robust security posture.
Matt ConranThe Evolution of Firewalls
Firewalls have come a long way since their inception. Initially, basic packet-filtering firewalls examined network traffic based on packet headers, such as source and destination IP addresses and port numbers. However, these traditional firewalls lacked the ability to analyze packet contents, leaving potential security gaps.
Stateful firewalls revolutionized network security by introducing advanced packet inspection capabilities. Unlike their predecessors, stateful firewalls can examine the entire packet, including the payload, and make intelligent decisions based on the packet’s state.
To comprehend the inner workings of a stateful firewall, imagine it as a vigilant sentry guarding the entrance to your network. It meticulously inspects each incoming and outgoing packet, keeping track of the state of connections. By maintaining knowledge of established connections, a stateful firewall can make informed decisions about allowing or blocking traffic.
Stateful firewalls offer several advantages over traditional packet-filtering firewalls. Firstly, they provide improved security by actively monitoring the state of connections, preventing unauthorized access and potential attacks. Secondly, stateful firewalls offer granular control over network traffic, allowing administrators to define specific rules based on protocols, ports, or even application-level information.
What is a Stateful Inspection Firewall?
Stateful inspection firewalls go beyond traditional packet filtering mechanisms by analyzing the context and state of network connections. They maintain a record of outgoing packets, allowing them to examine incoming packets and make informed decisions based on the connection’s state. This intelligent approach enables a higher level of security and better protection against advanced threats.
A stateful inspection firewall operates at the network and transport layers of the OSI model. It monitors the complete network session, keeping track of the connection’s state, including source and destination IP addresses, ports, and sequence numbers. By analyzing this information, the firewall can determine if incoming packets are part of an established or valid connection, reducing the risk of unauthorized access.
– Enhanced Security: Stateful inspection firewalls provide a stronger defense against malicious activities by analyzing the complete context of network connections. This ensures that only legitimate and authorized traffic is allowed through, minimizing the risk of potential attacks.
– Improved Performance: These firewalls optimize network performance by efficiently managing network traffic. By keeping track of connection states, they can quickly process incoming packets, reducing latency and enhancing overall network performance.
– Flexibility and Scalability: Stateful inspection firewalls can be customized to meet specific network security requirements. They offer flexibility in configuring security policies, allowing administrators to define rules and access controls based on their organization’s needs. Additionally, they can be seamlessly scaled to accommodate growing network infrastructures.
Firewall locations
In most networks and subnets, firewalls are located at the edge. The Internet poses numerous threats to networks, which are protected by firewalls. In addition to protecting the Internet from rogue users, firewalls prevent rogue applications from accessing private networks. To ensure that resources are available only to authorized users, firewalls protect the bandwidth or throughput of a private network. A firewall prevents worthless or malicious traffic from entering your network. A dam protects a river from flooding and overflowing, similar to how a dam works on a river. The dam prevents flooding and damage.
In short, firewalls are network functions specifically tailored to inspect network traffic. Upon inspection, the firewall decides to carry out specific actions, such as forwarding or blocking it, according to some criteria. Thus, we can see firewalls as security network entities with several different types.
The different firewall types will be used in other network locations in your infrastructure, such as distributed firewalls at a hypervisor layer. You may have a stateful firewall close to workloads while a packet-filtering firewall is at the network’s edge. As identity is now the new perimeter, many opt for a stateful inspection firewall nearer to the workloads. With virtualization, you can have a stateful firewall per workload, commonly known as virtual firewalls.
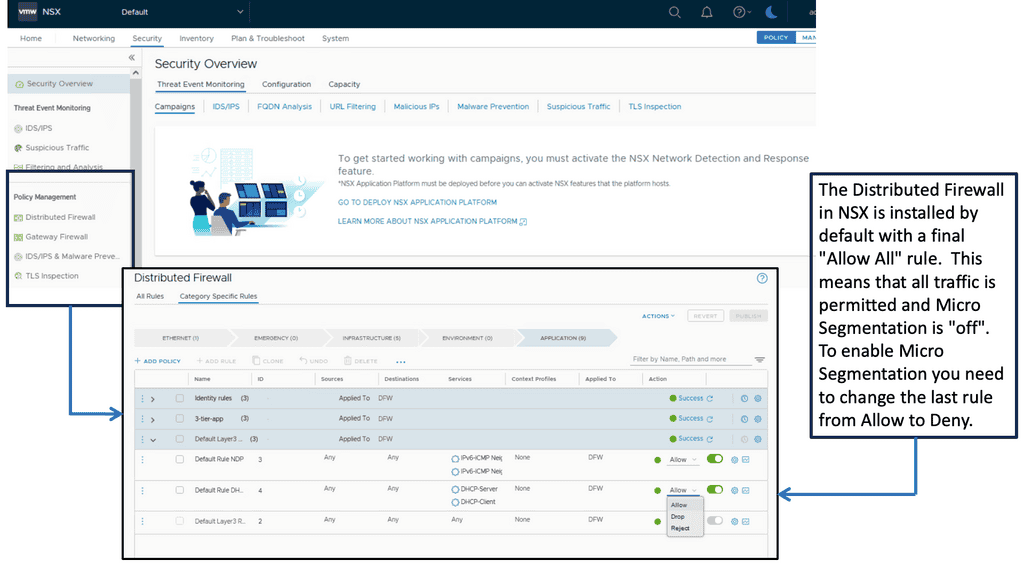
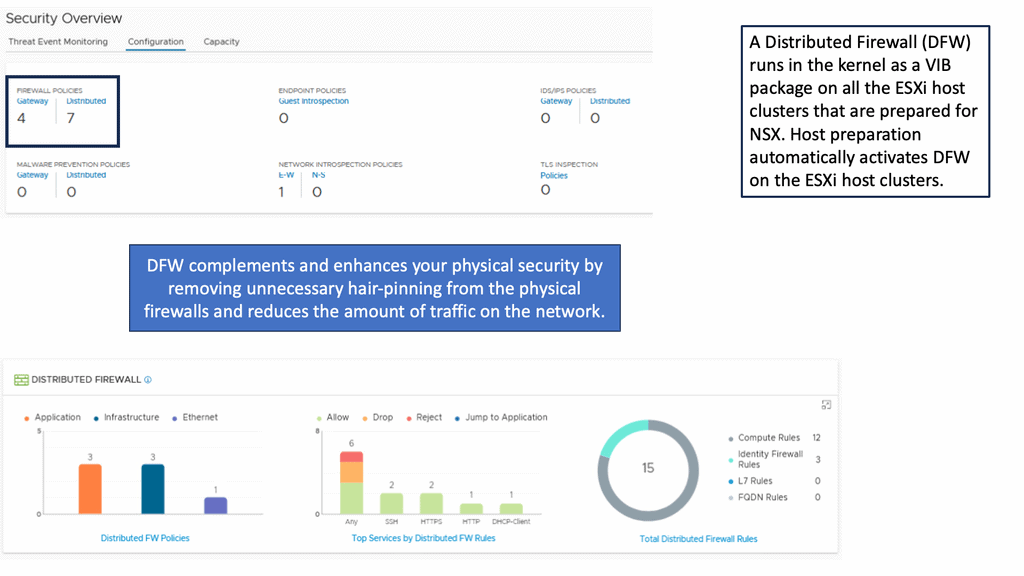
### What is VMware NSX Distributed Firewall?
VMware NSX Distributed Firewall is a software-defined networking (SDN) solution that provides advanced security features within the VMware NSX environment. Unlike traditional firewalls that operate at the network perimeter, the NSX DFW operates at the hypervisor level, allowing for micro-segmentation and granular control over network traffic between virtual machines (VMs). This innovative approach ensures that security policies are consistently enforced across the entire virtual environment.
### Key Features and Benefits
1. **Micro-Segmentation**: One of the standout features of NSX DFW is its ability to create micro-segments within the network. This means that even if a threat manages to breach the perimeter, its movement is restricted, minimizing potential damage.
2. **Granular Policy Control**: NSX DFW allows administrators to define security policies at a highly granular level. These policies can be based on a variety of factors, including VM attributes, user roles, and application types, ensuring that only authorized traffic is allowed.
3. **Scalability**: As your virtual environment grows, so does the need for robust security measures. NSX DFW scales seamlessly with your infrastructure, providing consistent protection without requiring additional hardware.
4. **Automation and Integration**: NSX DFW integrates with various VMware and third-party tools, allowing for automated policy enforcement and streamlined security management.
### Implementation Best Practices
1. **Define Clear Security Policies**: Before implementing NSX DFW, it’s essential to have a clear understanding of your organization’s security requirements. Define policies that align with these requirements and ensure they are consistently enforced.
2. **Regularly Update and Review Policies**: Cyber threats are constantly evolving, so it’s crucial to regularly review and update your security policies. This ensures that your network remains protected against the latest threats.
3. **Monitor and Analyze Traffic**: Utilize NSX DFW’s monitoring and analytics tools to gain insights into network traffic patterns. This information can help identify potential security vulnerabilities and inform future policy adjustments.


Example Technology: Linux Firewalling
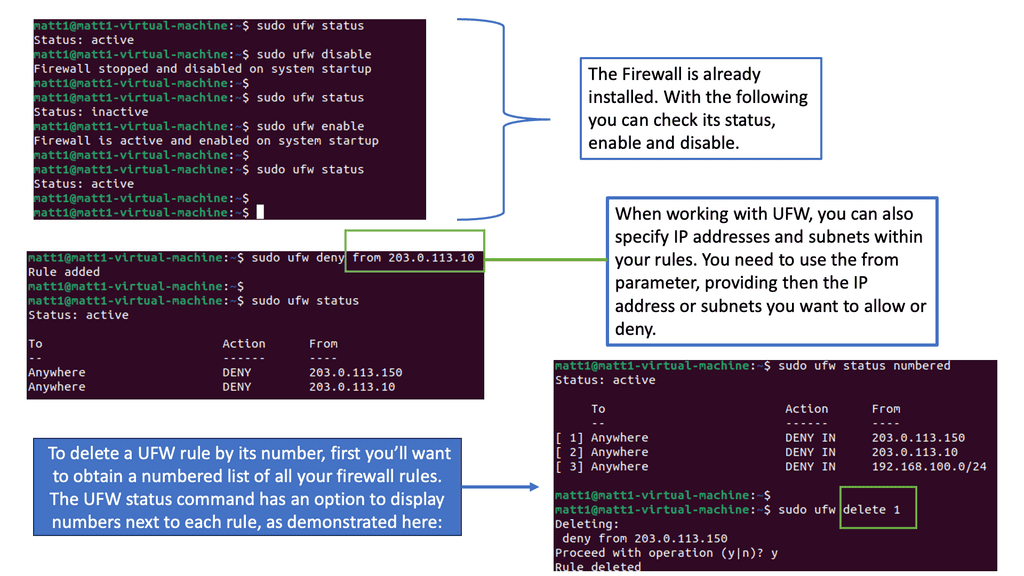
Understanding UFW
UFW, a front-end for IPtables, is a user-friendly and powerful firewall tool designed for Linux systems. It provides a straightforward command-line interface, making it accessible even to those with limited technical knowledge. UFW enables users to manage incoming and outgoing traffic, creating an additional layer of defense against potential threats.
UFW offers a range of features that enhance system security. Firstly, it allows you to create rules based on IP addresses, ports, and protocols, granting you granular control over network traffic. Additionally, UFW supports IPv4 and IPv6, ensuring compatibility with modern network configurations. Furthermore, UFW seamlessly integrates with other firewall solutions and can be easily enabled or disabled per your needs.
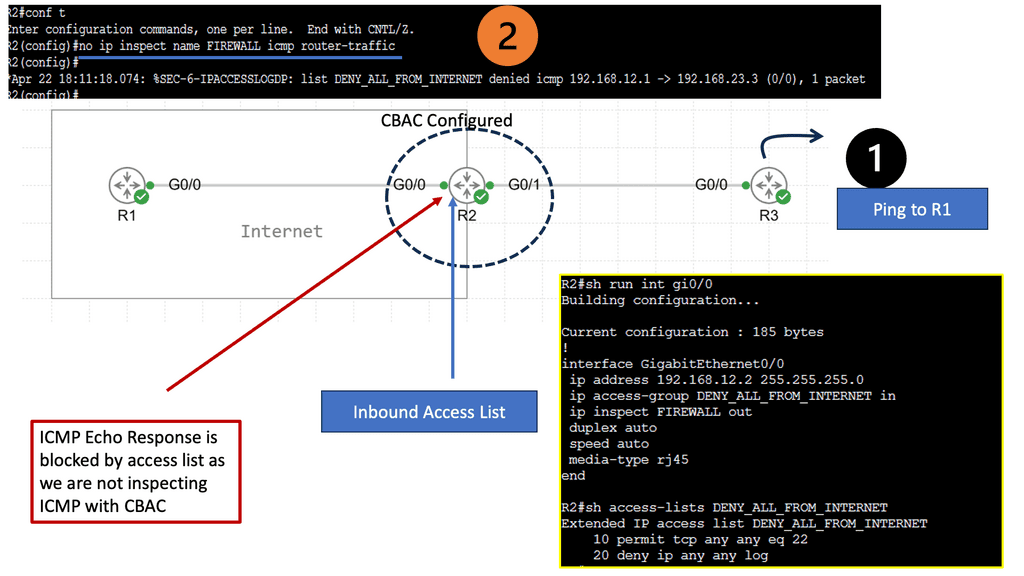
Example Firewall: CBAC Firewall
Cisco CBAC firewall goes beyond traditional stateless firewalls by inspecting and filtering traffic based on contextual information. It operates at the application layer of the OSI model and provides advanced security capabilities.
CBAC firewall offers a range of essential features that contribute to its effectiveness. These include intelligent packet inspection, stateful packet filtering, protocol-specific application inspection, and granular access control policies.
One of the primary objectives of CBAC firewalls is to enhance network security. By actively analyzing traffic flow context, they can detect and prevent various threats, such as Denial-of-Service (DoS) attacks, port scanning, and protocol anomalies.
Stateful Firewall
A stateful firewall is a form of firewall technology that monitors incoming and outgoing network traffic and keeps track of the state of each connection passing through it. It acts as a filter, allowing or denying traffic based on configuration. Stateful firewalls are commonly used to protect private networks from potential malicious activity.
The primary function of a Stateful Inspection Firewall is to inspect the headers and contents of packets passing through it. It maintains a state table that keeps track of the connection state of each packet, allowing it to identify and evaluate the legitimacy of incoming and outgoing traffic. This stateful approach enables the firewall to differentiate between legitimate packets from established connections and potentially malicious packets.
Unlike traditional packet filtering firewalls, which only examine individual packets based on predefined rules, Stateful Inspection Firewalls analyze the entire communication session. This means that they can inspect packets in the context of the whole session, allowing them to detect and prevent various types of attacks, including TCP/IP-based attacks, port scanning, and unauthorized access attempts.
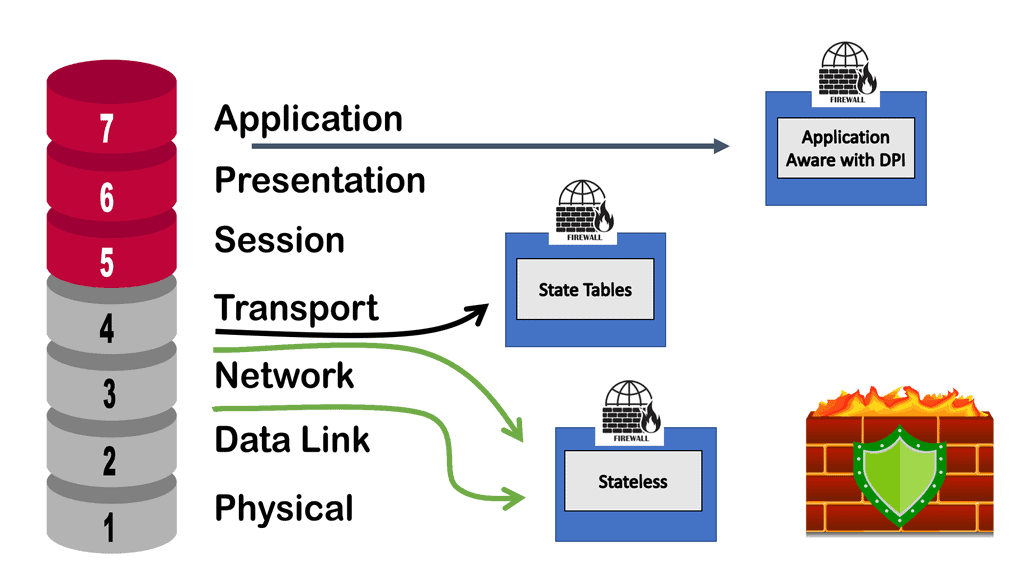
What is state and context?
A process or application’s current state refers to its most recent or immediate state. It is possible to compare the connection a user tries to establish with the list of connections stored in a firewall. A tracking device determines which states are safe and which pose a threat.
Analyzing IP addresses, packets, or other kinds of data can identify repeating patterns. In the context of a connection, for instance, it is possible to examine the contents of data packets that enter the network through a stateful firewall. Stateful firewalls can block future packets containing unsafe data.
Stateful Inspection
Stateful packet inspection determines which packets are allowed through a firewall. This method examines data packets and compares them to packets that have already passed through the firewall. Stateful packet filtering ensures that all connections on a network are legitimate. Static packet filtering on the network also examines network connections, but only as they arrive, focusing on packet header data. The firewall can only see where the data comes from and where it is going with this data.
Generally, we interact directly with the application layer and have networking and security devices working at the lower layers. So when host A wants to talk to host b, it will go through several communication layers with devices working at each layer. A device that works at one of these layers is a stateful firewall that can perform the stateful inspection.
Deep Packet Inspection (DPI)
Another significant advantage of Stateful Inspection Firewalls is their ability to perform deep packet inspection. This means that they can analyze the content of packets beyond their headers. By examining the payload of packets, Stateful Inspection Firewalls can detect and block potentially harmful content, such as malware, viruses, and suspicious file attachments. This advanced inspection capability adds an extra layer of security to the network.
Understanding Deep Packet Inspection
Deep Packet Inspection, often abbreviated as DPI, is a sophisticated technology used to monitor and analyze network traffic at a granular level. Unlike traditional packet inspection, which only examines packet headers, DPI delves deep into the packet payload, allowing for in-depth analysis and classification of network traffic.
DPI plays a vital role in network management and security. By inspecting the contents of packets, it helps network administrators identify and control applications, protocols, and even specific users. This level of visibility allows for better bandwidth management, traffic shaping, and the implementation of security measures to protect against malicious activities and intrusions.
Applications of DPI
1. Network Security: DPI enables the detection of malicious activities such as intrusions, malware, and unauthorized access attempts. It helps in identifying and preventing data breaches by monitoring and analyzing network traffic patterns in real-time.
2. Quality of Service (QoS): DPI helps network administrators prioritize and allocate network resources based on specific applications or services. By understanding the nature of traffic passing through the network, DPI can optimize bandwidth allocation, ensuring a seamless and reliable user experience.
3. Regulatory Compliance: In certain industries, such as finance or healthcare, strict regulations govern data privacy and security. DPI assists organizations in meeting compliance requirements by monitoring and controlling network traffic.
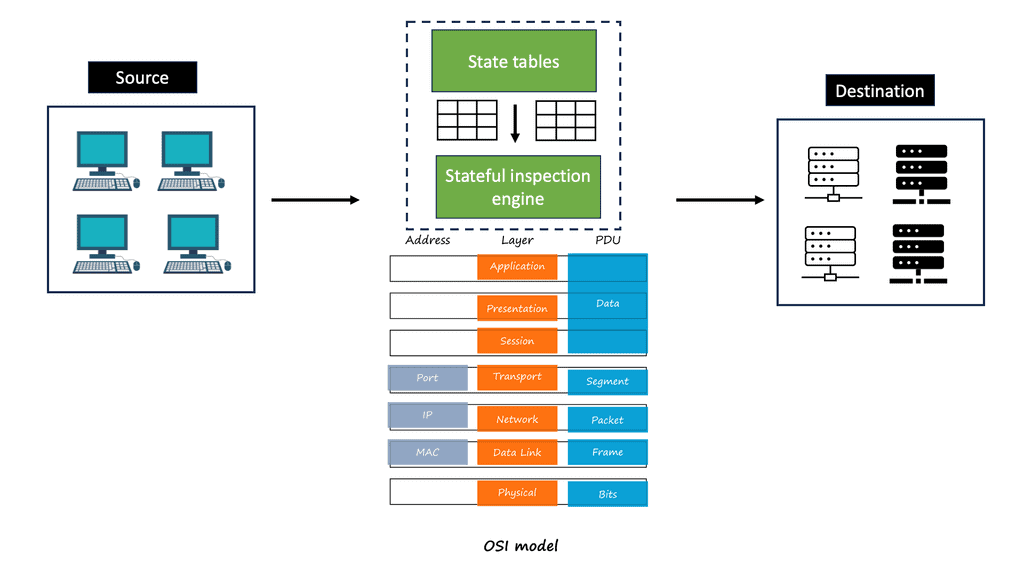
Combining Security Features
They can be combined with other security measures, such as antivirus software and intrusion detection systems. Stateful firewalls can be configured to be both restrictive and permissive and can be used to allow or deny certain types of traffic, such as web traffic, email traffic, or FTP traffic. They can also control access to web servers, databases, or mail servers. Additionally, stateful firewalls can detect and block malicious traffic, such as files, viruses, or port scans.
Transport Control Protocol (TCP)
TCP allows data to be sent and received simultaneously over the Internet. Besides assisting in transmitting information, TCP also contains data that can cause a connection to be reset (RST), resulting in its termination. TCP uses the FIN (finish) command when the transmission should end. When data packets reach their destination, they are grouped into understandable data.
Stateful firewalls examine packets created by the TCP process to keep track of connections. To detect potential threats, a stateful inspection firewall uses the three stages of a TCP connection: synchronize (SYN), synchronize-acknowledge (SYN-ACK), and acknowledge (ACK). During the TCP handshake, stateful firewalls can discard data if they detect bad actors.
Three-way handshake
During the three-way handshake, both sides synchronize to establish a connection and then acknowledge one another. Each side transmits information to the other as part of this process, which is inspected for errors. In a stateful firewall, the data sent during the handshake can be examined to determine the packet’s source, destination, sequence, and content. The firewall can reject data packets if it detects threats.
Google Compute Security
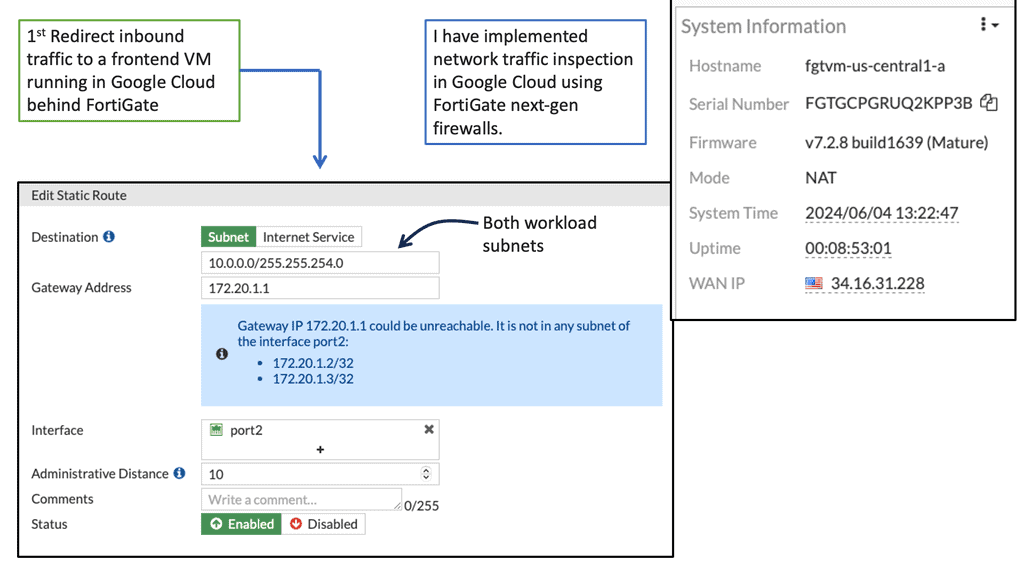
Google Compute Engine allows businesses to leverage the cloud for scalable and flexible computing resources. However, with this convenience comes the need for stringent security measures. Cyberattacks and data breaches pose a significant risk, making it crucial to implement robust security protocols to safeguard your Google Compute resources.
FortiGate is a comprehensive network security platform that offers advanced threat protection, secure connectivity, and granular visibility into your network traffic. With its cutting-edge features, FortiGate acts as a shield, defending your Google Compute resources from malicious activities, unauthorized access, and potential vulnerabilities.
Advanced Threat Protection: FortiGate leverages industry-leading security technologies to identify and mitigate advanced threats, including malware, viruses, and zero-day attacks. Its robust security fabric provides real-time threat intelligence and proactive defense against evolving cyber threats.
Secure Connectivity: FortiGate ensures secure connectivity between your Google Compute resources and external networks. It offers secure VPN tunnels, encrypted communication channels, and robust access controls, enabling you to establish trusted connections while preventing unauthorized access.
Granular Visibility and Control: With FortiGate, you gain granular visibility into your network traffic, allowing you to monitor and control data flows within your Google Compute environment. Its intuitive dashboard provides comprehensive insights, enabling you to detect anomalies, identify potential vulnerabilities, and take proactive security measures.
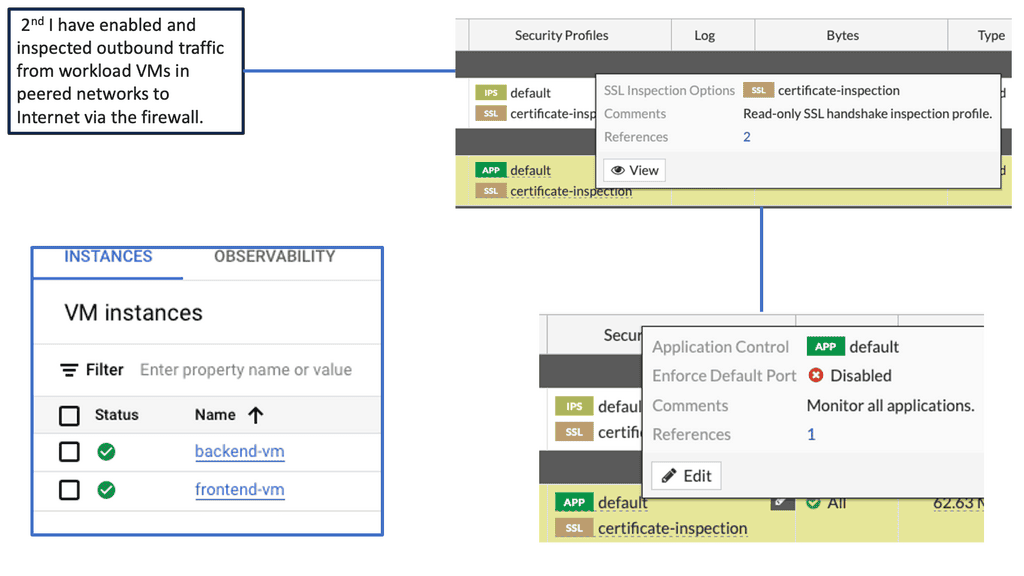
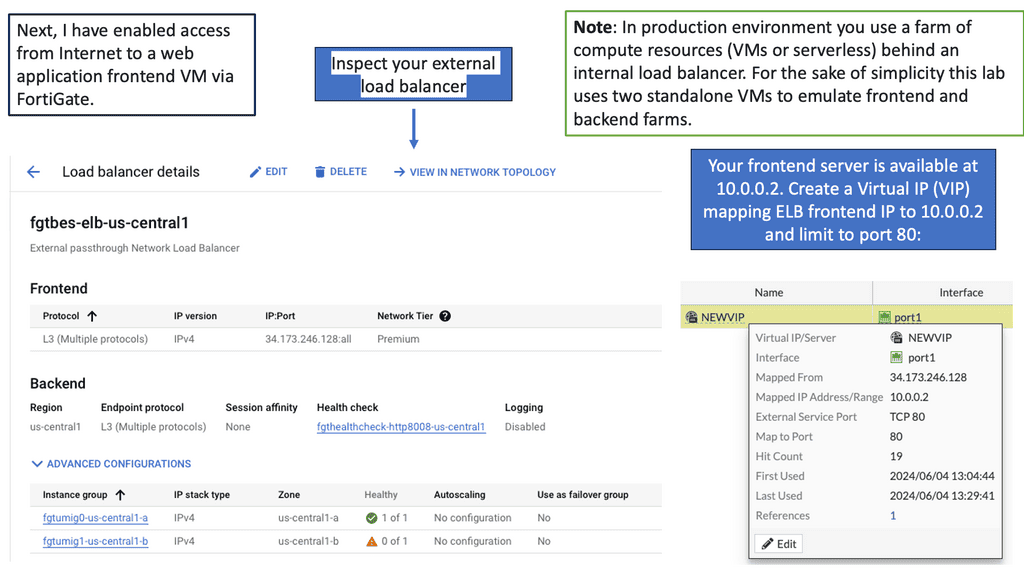
The Benefits of Deep Packet Inspection with FortiGate
Enhanced Network Visibility: By leveraging DPI with FortiGate, organizations gain unparalleled visibility into their network traffic. Detailed insights into application usage, user behavior, and potential security vulnerabilities allow for proactive threat mitigation and network optimization.
Granular Application Control: DPI enables organizations to enforce granular application control policies. By identifying and classifying applications within network traffic, FortiGate allows administrators to define and enforce policies that govern application usage, ensuring optimal network performance and security.
Intrusion Detection and Prevention: With DPI, FortiGate can detect and prevent intrusions in real-time. By analyzing packet content and comparing it against known threat signatures and behavioral patterns, FortiGate can swiftly identify and neutralize potential security breaches, safeguarding sensitive data and network infrastructure.
Before you proceed, you may find the following helpful post for pre-information: